In the previous topic, we got idea that how AES encrypts/decrypts plaintext with 16 bytes length. However, what happens when the plaintext exceeds 16 bytes?
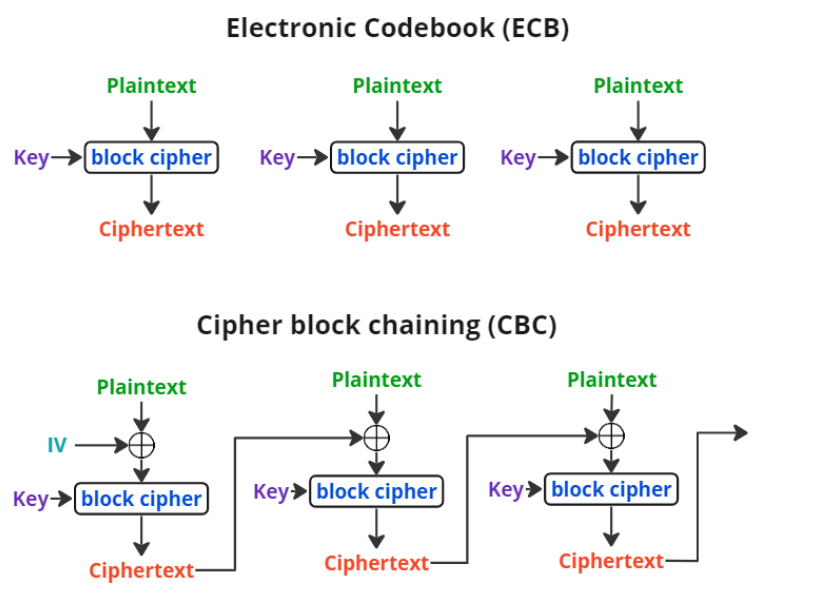
ECB (Electronic Codebook):
- In ECB mode, the plaintext is divided into fixed-size blocks (usually 16 bytes each).
- Each block is encrypted independently using the same key.
- The same plaintext block will always produce the same ciphertext block.
- However, this mode is not secure for large messages because identical plaintext blocks result in identical ciphertext blocks, which can leak information.
- ECB mode does not provide any diffusion (spreading out the influence of one plaintext byte over multiple ciphertext bytes).
CBC (Cipher Block Chaining):
- In CBC mode, each plaintext block is XORed with the previous ciphertext block before encryption.
- The first block (A fixed-size random value usually 128 bits or 16 bytes, also called the initialization vector or IV) is XORed with the plaintext.
- This chaining ensures that identical plaintext blocks produce different ciphertext blocks.
- CBC provides better security than ECB because it introduces diffusion. However, it requires an IV, which must be unpredictable and unique for each message.
PKCS#7
PKCS#7 padding adds a sequence of bytes to the end of the data where each byte’s value is the same as the total number of padding bytes added.
Encryption
- Initialization
- Plaintext: “This is a longer message that exceeds 16 bytes.”
- Key: “this is my srkey”.
- Initialization Vector (IV): A random 16-byte value.
- Padding
using PKCS#7 padding we have the result: Padded plaintext: “This is a longer message that exceeds 16 bytes.\x01”. - Encryption
- Divide padded text into blocks.
Block 0: “This is a longer”
Block 1: ” message that ex”
Block 2: “ceeds 16 bytes.\x01” - XOR first block with IV
XOR result: 54696b70246c752769296664626a6b7d - Encrypt blocks
Block 0: c76da1bda3a7e778962734b8393bdbbf
Block 1: ed13b5a44c618335f75e89da54d044c8
Block 2: bf6fa8220a908926b3f1ba72c91c05bb
- Divide padded text into blocks.
- Ciphertext
Concatenate the encrypted blocks together to obtain the ciphertext.
c76da1bda3a7e778962734b8393bdbbfed13b5a44c618335f75e89da54d044c8bf6fa8220a908926b3f1ba72c91c05bb
Decryption
- Initialization
Initialization Vector (IV): is first 16 bytes of cipher text.
iv: c76da1bda3a7e778962734b8393bdbbf - Decryption
- Divide ciphertext into blocks
Block 0: c76da1bda3a7e778962734b8393bdbbf
Block 1: ed13b5a44c618335f75e89da54d044c8
Block 2: bf6fa8220a908926b3f1ba72c91c05bb - Decrypt first block then XOR with IV
XOR result: 546869732069732061206c6f6e676572. This also is the Block 0. - Decrypt rest blocks and concatenate with Block 0, we have:
Block 0: “This is a longer”
Block 1: ” message that ex”
Block 2: “ceeds 16 bytes.\x01”
- Divide ciphertext into blocks
- Remove padding
After concatenate the blocks and remove the padding we have:
Plain text: “This is a longer message that exceeds 16 bytes.”
Here is a simple CBC demo. Thanks for reading!
References
Block cipher mode of operation – Wikipedia
