AES also known by its original name Rijndael is a symmetric block cipher algorithm, which means the sender and receiver use the same key for encryption and decryption.
AES operates on a 4 × 4 column-major order array of 16 bytes b0, b1, …, b15 termed the state.

The key size of AES specifies the number of transform rounds that convert the input (plain text) to the output (cipher text).
- 10 rounds for 128-bit keys.
- 12 rounds for 192-bit keys.
- 14 rounds for 256-bit keys.
Encryption
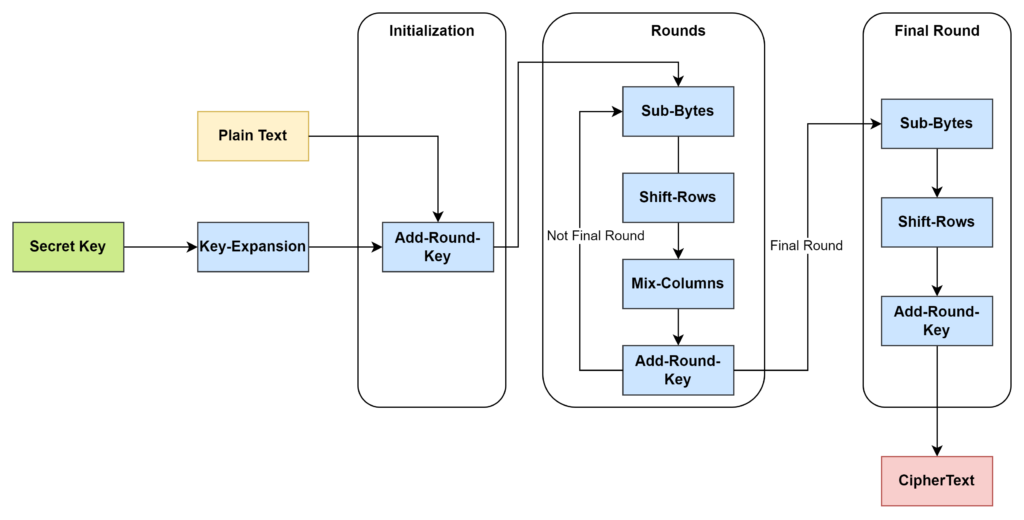
Key-Expansion – Each round uses a different key that is transformed from the secret key. The round keys are generated at the beginning of the encryption.
Each round comprises of 4 steps:
- Sub-Bytes: Each byte is replaced with another according to a lookup table.
- Shift-Rows:
- The first row is not shifted.
- The second row is shifted once to the right.
- The third row is shifted twice to the right.
- The fourth row is shifted thrice to the right.
- Mix-Columns:
- In this step, we multiply each column of the state array by a fixed matrix (called the Mix Columns matrix). The result is a new column for the subsequent state array.
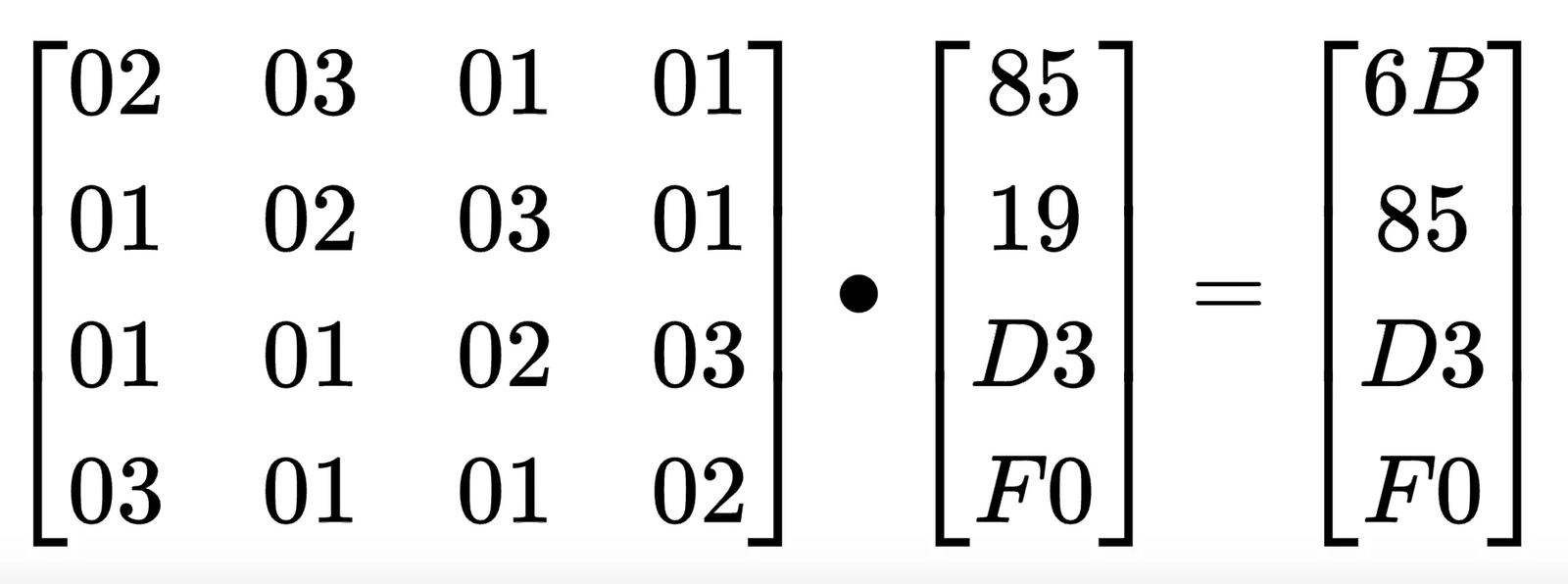
- The Mix Columns matrix is defined as:

- To calculate the new column we do:
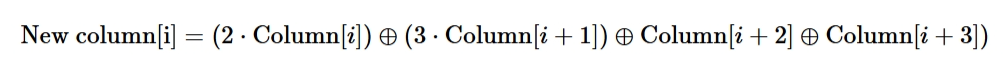
where:- ⊕ represents the bitwise XOR operation.
- ⋅ represents multiplication in the finite field (GF(2^8)).
- Example
- Add-Round-Key
we perform an XOR operation the result of step 3 with the round key of the next round, then proceed back to Sub-Bytes step to begin the next round. This cycle is repeated until the final round is reached.
Note: In the final round, we skip the Mix-Columns step.
Decryption
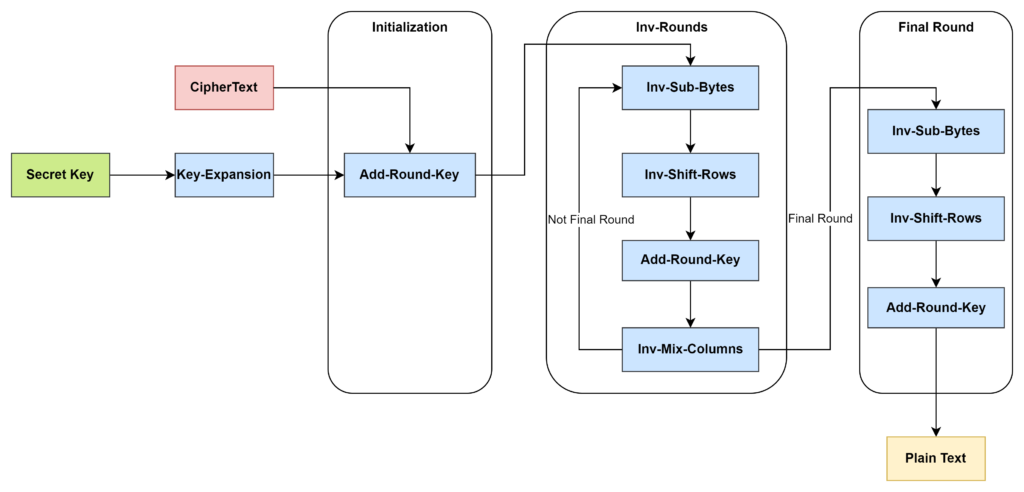
First, we generate the keys similar with the Key-Expansion step in the encryption.
Next, we do the invert steps:
- Add-Round-Key
Do same operation with the Add-Round-Key of the encryption process. - Invert-Sub-Bytes
Each byte is replaced with another according to a Inverse S-box. - The first row is not shifted.
- The second row is shifted once to the left.
- The third row is shifted twice to the left.
- The fourth row is shifted thrice to the left.
- Invert-Mix-Columns
We also do the same actions with the Mix-Columns step in the encryption, but using the invert Mix Column Matrix.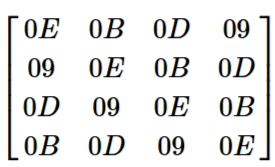
Note: In the final round, we also skip the Inv-Mix-Columns step.
Here is a simple demo. Thank for reading!
References
Advanced Encryption Standard – Wikipedia
Advanced Encryption Standard (AES) – GeeksforGeeks
AES Encryption: Secure Data with Advanced Encryption Standard (simplilearn.com)
Online AES Encryption / Decryption | Anycript
